All You need to know about Ransomware
What is Ransomware?
Ransomware is a category of malware which disables the
functionality of your computer by restricting your access to it in some way.
Then, it demands a ransom to be paid to the malware author to restore the
system’s functionality. The ransomware program usually locks a computer and
displays various law enforcement images to intimidate and extort money from
victims. In addition to locking you out of your computer, some ransomware will
encrypt and hide your personals files so that you don’t have access to them
anymore.
What does Ransomware
do?
There are different types of ransomware. However, all of
them will prevent you from using your PC normally, and they will all ask you to
do something before you can use your PC.
They can target any PC users, whether it’s a home
computer, endpoints in an enterprise network, or servers used by a government
agency or healthcare provider.
Ransomware can:
·
Prevent you from accessing Windows.
·
Encrypt files so you can't use them.
·
Stop certain apps from running (like your web
browser).
Ransomware will demand that you pay money (a “ransom”) to
get access to your PC or files. Some of them also make you complete surveys. There
is no guarantee that paying the fine or doing what the ransomware tells you
will give access to your PC or files again.
Historical Background
Ransomware is not a new phenomenon. The first instance of
ransomware appeared back in 1989 which was known as the PC Cyborg Trojan (also
known as Aids Info Disk (AIDS)). The infamous Trojan replaced the autoexec.bat
file on the infected machine and would count the number of times a computer had
booted. Once the system’s boot count reached 90, the Trojan would hide
directories and change all of the filenames on the drive C:\, making the system
unusable. To restore the system’s functionality, the Trojan demanded that the
user pay $189 to the "PC Cyborg Corporation." Although ransomware is
not new, it has drastically increased since 2005. Ransomware attacks were initially
popular in Russia, but over the past few years, the number of ransomware
attacks has been increasing worldwide.
Ransomware types
and details
There are two types of ransomware – lockscreen ransomware
and encryption ransomware.
Lockscreen ransomware shows a full-screen message that
prevents you from accessing your PC or files. It says you have to pay money (a
“ransom”) to get access to your PC again.
Encryption ransomware changes your files so you can’t
open them. It does this by encrypting the files – see the Details for
enterprises section if you’re interested in the technologies and techniques
we’ve seen.
Older versions of ransom usually claim you have done
something illegal with your PC, and that you are being fined by a police force
or government agency.
These claims are false. It is a scare tactic designed to
make you pay the money without telling anyone who might be able to restore your
PC.
Newer versions encrypt the files on your PC so you can’t
access them, and then simply demand money to restore your files.
Ransomware can get on your PC from nearly any source that
any other malware (including viruses) can come from. This includes:
·
Visiting unsafe, suspicious, or fake websites.
·
Opening emails and email attachments from people
you don’t know, or that you weren’t expecting.
·
Clicking on malicious or bad links in emails,
Facebook, Twitter, and other social media posts, instant messenger chats, like
Skype.
It can be very difficult to restore your PC after a
ransomware attack – especially if it’s infected by encryption ransomware.
How Ransomware is
different from other Malware?
Ransomware has
some key characteristics that set it apart from other malware:
·
It features unbreakable encryption, which means that you can’t decrypt the
files on your own (there are various decryption tools released by cyber
security researchers – more on that later);
·
It has
the ability to encrypt all kinds of files, from documents to pictures,
videos, audio files and other things you may have on your PC;
·
It can scramble your file names, so you can’t know which data was
affected. This is one of the social engineering tricks used to confuse and
coerce victims into paying the ransom;
·
It will add a different extension to your files, to sometimes signal a
specific type of ransomware strain;
·
It will display an image or a message that lets you know your data has been
encrypted and that you have to pay a specific sum of money to get it back;
·
It requests
payment in Bitcoins, because this crypto-currency cannot be tracked by
cyber security researchers or law enforcements agencies;
·
Usually, the ransom payments have a time-limit, to add another level of
psychological constraint to this extortion scheme. Going over the deadline typically
means that the ransom will increase, but it can also mean that the data will be
destroyed and lost forever.
·
It uses
a complex set of evasion techniques to go undetected by traditional
antivirus (more on this in the “Why ransomware often goes undetected by
antivirus” section);
·
It often
recruits the infected PCs into botnets, so cyber criminals can
expand their infrastructure and fuel future attacks;
·
It can
spread to other PCs connected in a local network, creating further
damage;
·
It frequently
features data exfiltration capabilities, which means that ransomware can
extract data from the affected computer (usernames, passwords, email addresses,
etc.) and send it to a server controlled by cyber criminals;
·
It sometimes
includes geographical targeting, meaning the ransom note is translated
into the victim’s language, to increase the chances for the ransom to be paid.
Popular Ransomware
Variants (Infection Methods)
There are many variants of ransomware out there, but it
can be loosely classified into four categories:
1. SMS Ransomware
This type of ransomware locks your computer and displays
a ransom message with a code. To unlock your computer, you are instructed to
send the code via text message to a premium-rate SMS number to receive the
corresponding code to unlock it.
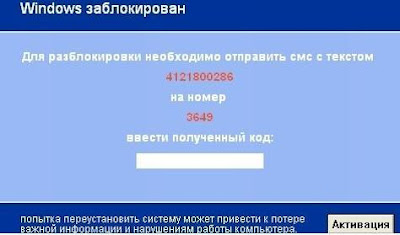
Below is an example of a lock screen (which claims to be
from Microsoft) displayed by one of the SMS ransomware variants. The lock
screen instructs victims to send a code (4121800286) to 3649 (which is a
premium-rate SMS number) in order to receive the Windows® activation code.
2. Winlocker
This variant of ransomware also locks your computer, but
it displays a more intimidating ransom message which appears to be from your
local law enforcement agency. Unlike SMS ransomware, this particular kind
instructs you to pay through an online payment system such as Ukash,
Paysafecard, or Moneypak.
Below is an example of a recent variant of Winlocker
ransomware. The lock screen indicates that the FBI has locked down the user’s
computer for committing some sort of cybercrime. The lock screen also includes
instructions on how the user can pay for the fine via an online payment
service. This type of malware is more commonly known as the “FBI Virus” or
“Moneypak Virus”.
3. File Encryptors
This kind of ransomware can encrypt your personal files
and folders using complex encryption algorithms to make your computer’s data
unusable. The malware author then demands that you pay for the decryption key
using one of the online payment systems mentioned above. The ransomware often
leaves a file (or a “ransom note”) on the victim’s machine with payment
instructions. This type of ransomware may or may not lock your screen.
4. MBR Ransomware
This is another popular variant of ransomware, but it
goes one step farther than the other three types mentioned above in terms of
how the computer is locked. MBR Ransomware can change your computer's Master
Boot Record (MBR) and interrupts the normal boot process. The MBR is a
partition on your computer's hard drive that allows the operating system to
load and boot. When this ransomware strikes, the ransom message is displayed as
soon as the computer is turned on, meaning that you do not get the chance to
load the operating system to remove the infection and repair your system.
MBR Ransomware may look scary, but this type of infection
can easily be removed. The ransom message often says that the files have been
encrypted, but in reality, they are not.
Examples of
Ransomware Attack
One of the recent ransomware that caused the most harm
was in 2013, is known as CryptoLocker. The brain behind this malware was a
Russian hacker by the name of Evgeniy Bogachev. The malware, when injected into
a host system, scans the hard drive of the victim and targets specific file
extensions and encrypts them. These could be important files or programs that
user really needs, like documents, programs or keys. The encryption is done
using a 2048-bit RSA key pair, with the private key uploaded to command and
control server. The programs then threaten the user that it will delete the
private key, unless a payment in form of bitcoins is done within three days.
A 2048 RSA key is indeed a big protection, and it will
take a normal desktop PC several thousands of years to break the key using
brute force. The user, helpless agrees to pay the amount in order to get the
files back.
It is estimated that this CryptoLocker Ransomware
procured at least $3 million before it was shut down.
While that’s a lot of money, another ransomware by the
name of WinLock was able to procure $16 million in ransom. While it did not
encrypt the system like CryptoLocker, what it did was to restrict the app
access of the user and show pornographic images instead. The user was then
forced to send a premium rate SMS, costing around $10 to get a code to unlock
the ransomware.
All these attacks were way back in 2013.
However, the most recent attack was by an updated form of
ransomware, called CryptoWall 2.0. According to a New York Times report this
ransomware attacked PCs in a fashion similar to CryptoLocker, and attacked especially
important files in victim’s system, like tax receipts, bills etc. Then it
demanded a ransom of $500. The price of the ransom doubled after a week, and
further a week later, the unlock key was deleted.
Recently according to some reports, CryptoWall has been
updated to version 3.0, and apparently it has become more dangerous than ever.
This version of CryptoWall encrypts the user files by a system of intelligent
scanning, and then generates a unique link for the user. As a protection to
preserve anonymity of the attackers and make government agencies harder to
arrest them, this ransomware is not only using Tor, but also I2P which makes it
really hard to track them.
While it may sound ironic, but CrytoWall has really good
customer service. As they have to maintain a reputation to get more and more
money, they provide decryption keys to the user as quickly as possible, often
within hours after the ransom has been paid out.
How to Protect Your Computer Against Ransomware
The ways to protect your computer from ransomware are
similar to the ways to protect your computer from any kind of malware. Here are
a few rules to remember to avoid malware attacks:
1. Always backup your data: Whether it’s a
ransomware or any other malware attack, there’s always a possibility of losing
your data. Backup your data on a regular basis and keep those files in a secure
place away from your computer so that you can restore it in an event of data
loss. It is recommended to have 2 backups of your data: on an external hard
drive and in the cloud – Dropbox/Google Drive/etc. Note that the Dropbox/Google
Drive/OneDrive/etc. application on my computer should not turn on by default. You
should only open them once a day, to sync your data, and close them once this
is done.
2. Think before you click: Do not open email
attachments that you were not expecting or click on links on suspicious
websites. If you see an email from a company that is trying to get you to open
an attachment to receive something like money or a parcel, ignore that email
because it may be an attempt to get you to install bad software. Often fake
emails and webpages have bad spelling, or just look unusual. Look out for
strange spellings of company names (like “PayePal” instead of “PayPal”) or
unusual spaces, symbols, or punctuation (like “iTunesCustomer Service” instead
of “iTunes Customer Service”).
3. Secure your PC: Make sure your computer is
protected with anti-virus/anti-malware software.
4. Stay up-to-date: Make sure that all of your
security programs, operating systems and other applications are up-to-date.
Also, make sure that automatic updating is turned on.
5. Don’t pay: If you believe that you are a victim
of a ransomware attack, do not panic and, more importantly, do not pay. Even if
you make the payment, there is no guarantee that your computer’s functionality
or its data will be restored. Instead, contact your local cyber law enforcement
agency.
Sources and
Additional Information: